Black Hawk American Airlines Crash is Deemed a Terrorist Attack, Criminal Figures Identified
Part of a series of terrorist attacks by the Deep State actors jointly with the Mafia in one of the largest scandals involving corruption in the Federal Government
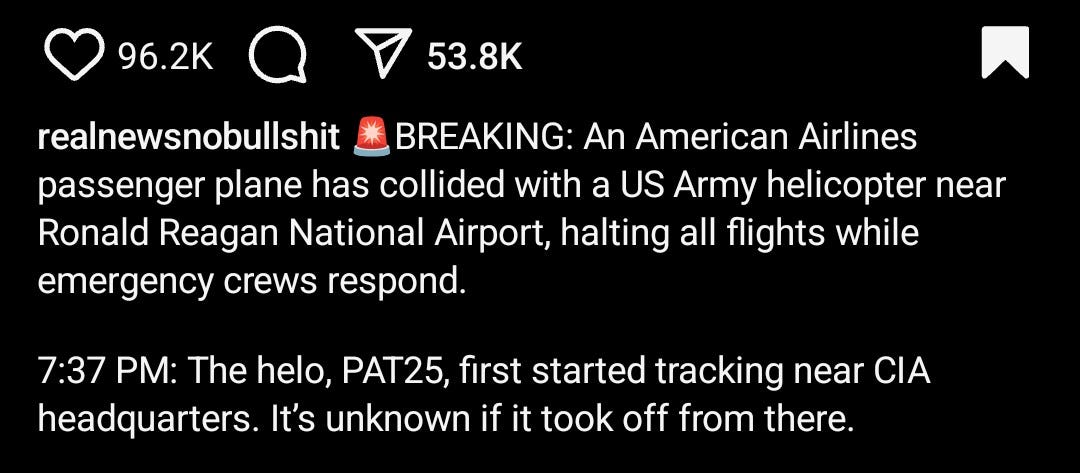
The Black Hawk was “electronically hijacked” in a way that "locked" the aircraft in its direction and "disabled" its radio communications capabilities.
The attack has been deemed to be a terrorist attack of retaliation in nature against CIA particularly in one of the largest corruption and organized crime scandals in history involving the FBI and Mafia Leaders connected to the Bureau. This event adds to the list of attacks motivated for in the same case.
Don’t be surprised, the Bureau is protecting its corrupt business with those Mafia leaders that is standing on bribery and “covertly manipulates” the American people through “Acts of Terrorism” against any authority that opposes them. Read disclaimers at the bottom.
Unlike ISIS that often directly attributes a terrorist attack to them, the criminal actors employ elements, similar to pieces of a puzzle that as a result when put together by an agency such as the CIA, these collectively form a holistic picture attributing the incident to them only in an indirect way, intending to evade accountability.
In other words, the criminal actors scatter those pieces and the CIA, within the framework of the case put those pieces together which as a result completes the picture that attributes each incident to them. This article outlines the layout of these elements and puzzle pieces while providing the public with a new angle of insights that had not been previously presented.
The details even go to the choice of the Military aircraft model, which "Airline", the location and even the “number” of the "runway" at the airport.
This is why we have to evaluate what constitutes a valid and admissible evidence nowadays accordingly with the continuous advancements across all industries and the level of sophistication and complexity of crimes can reach. You can't have a type of evidence that you're using in cases since the 60s and expecting to apply the same and not willing to accept any other form of evidence in 2025.
Involving a Former Boeing Official
Adel Andraws
The incident came only 4 days after a report was made referencing a former high-ranking Boeing official who is maliciously involved in the case, Adel Andraws (pictured below).
The nature of that particular report was a message that a CIA asset has communicated a message with other assets (witnesses) from the community that involves such corruption linked to the FBI which has pointedly referenced Adel’s career at "Boeing". Adel is also referred to by a Mafia Leader in the scandal case. Link to the full context on Adel’s post is added at the bottom of this article.
CIA Asset
An individual (asset, pictured below) who’s indirectly linked to the CIA and his interactions are being leveraged as a medium by those criminal actors to relay those pieces of the puzzle towards their terrorist attacks.
Here are the details of each of those pieces based on the FBI corruption scandal. Please maintain an open-minded mentality since this case encompasses complex technological and technological advancements.
Elements Surrounding The Terrorist Attack
Black Hawk
Target the individual (the CIA asset) with videos from "Black Hawk Down" movie over YouTube through manipulated organic feed, next auto-played videos and other techniques. The intent is to ensure that those videos from the "Black Hawk Down" movie standout and are subtle. Puzzle piece 1.
The Deadliest Attack Since 9/11
The event is reportedly the deadliest since 20 years ago, particularly 9/11. But we can see that 9/11 event has been referenced in the case several times and the date has been used indirectly by primary criminal actors to imply for threats, as documented here.
Puzzle piece 2
American Airlines
The same exact airline company that the individual used to fly over to a foreign country (in the meantime) in order not to be unlawfully prosecuted by the FBI.
Puzzle piece 3
But also, they targeted him with a person who looked almost identical to an individual connected to the case, namely Curt Altig. They're just laying out the puzzle pieces.
Puzzle piece 4
AA
Are the initials of the Airline name, and initialing is a common practice particularly in Intelligence as it appears. Hence, elements (companies in particular) sharing the same initials can be used to target the victim who’s also the CIA asset as a preliminary futuristic implication and a piece of puzzle, subsequently gathered by CIA.
Such targeting can come through that company's trucks having a large "AA" to precisely target the victim on road and might as well send them targeted ads over social media just to reinforce the targeting.
Again, these are the elements of the puzzle that we can call it in a reverse way.
Puzzle piece 5
Search and Rescue
The famous text had been initially reported in the case in a mailed report to the CIA that was made public in a later date where it had targeted the individual in a malicious way through a targeted Toyota 4 Runner, same make, model and color as the vehicle owned by one of the main criminal actors, namely Ramy Gewida (pictured below) who's the nephew to the former high-rank Boeing employee, Adel Andraws.
Additionally, in another mailed report to CIA, also was made public, another successor instance of a pickup truck carrying a "Helicopter" on its back targeting the CIA individual on the street of "his residence" in Washington state where that "Helicopter" had a large text as "Search and Rescue" on it.
More importantly, the truck driver looked at the CIA individual in a harassing manner for a prolonged amount of time and made a humiliating smile expression before turning right on the intersection and even though he was on the other side of the street that did not involve an intersecting traffic with the CIA asset.
It seemed as if it was a “do you see me?” question by the driver that he didn’t leave the scene until the CIA asset acknowledged him, which is why this was recognized as a targeting instance with a “significance” linking both “Search and Rescue” and “Helicopters”.
The “timestamps” of those documentations included in the reports made to CIA which were prior to the attack is another strong piece of artifact contributing towards the holistic evidence of the attack incident, alongside the other pieces.
Puzzle piece 6
River
The “Potomac River” where the aircrafts crashed over.
As seen in previous published videos of the degree of sophistication in altering the phone swipe keyboard of the CIA individual particularly when documenting events connected to the corruption scandal case, “River” here is a commonly “substituted keyword” that replaces the name of one of the main criminal individuals in the case, “Robert”.
Such inadvertent substitution is applied through cybercrime whenever the CIA-connected individual swipes his phone's keyboard to generate his name. Hence, swiping the keyboard to generate “Robert” results in an inadvertent substitution by the keyword "River" instead.
They just threw another piece of the puzzle with an indirect attribution to one of the main criminals in the case.
Puzzle piece 7
Aligned With Kash Patel’s Confirmation Hearing Date
Jan 30th, 2025
In the case that reports FBI corruption.
Have the attack align exactly with the date that Trump's nominee "Kash Patel" is having his confirmation hearing on that will subsequently lead to the replacement of "Christopher Wray" and the cleanse of the corruption in the bureau as declared by Kash several times as well as Trump.
What a perfectly aligned date among all the other puzzle pieces that the corrupt bureau will still say "coincidences" that constitute no evidence but if it was another case that works to their favor, those same exact "coincidences" as they call them would have been considered as evidence. They might as well elaborate by calling them "forensic evidence", only when it works for them and for the "dollars".
Puzzle piece 8
Wichita
Wichita is the location that the American Airlines has originally took off from.
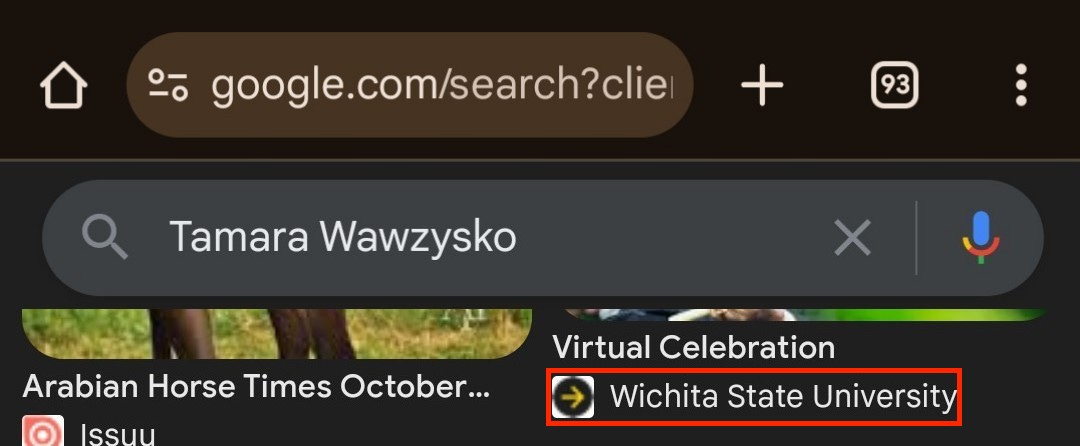
The case reportedly involves an individual from Ford Motor Company that the CIA partnered with to engage in the case initially as explained in the other case articles. The individual's name is "Tamara Wawzysko".
As we continue to monitor and surveil the CIA individual in real-time we observed that he looked up that individual by their name on Google and the search engine displayed search results for a woman with a matching name titling it "Wichita", the same location as the attack occurred at.
But in fact we have a portfolio constructed on that individual's habits and we have intel on the name of the individuals who could be part of the project at Ford that the CIA intends to engage in the case through.
Based on that we expect that the CIA individual will look that person up on Google and do as the other co-workers at Ford.
We are so corrupt that we can alter anything on any platform. Have a search results for a woman comes up on Google when the term "Tamara Wawzysko" is searched and assign a title that includes "Wichita" to it. Because “every detail” matters.
I'm just giving you an idea of how things get planned from the very beginning, this is a reverse overview on it.
Puzzle piece 9
AE
The initials of American Eagle (the alternative or former name of the airlines). With each time that the individual types a keyword on the keyboard that ends in "ase" such as "Rephrase", we want it to be typed as "Rephrae" instead, dropping the "s" letter and with the repetition of such alteration of keywords and inadvertent or involuntary typos (aside of the methods these are imposed through) that will make the ending of such keyword is "ae" obvious and stands out that can represent a suffix, similar initialing.
Video Preview Failed to Load? Click Here
They just created a “lead” element and CIA will register this as an element with significance; hence, it can be correlated to the terrorist attack on the American Eagle flight.
Puzzle piece 10
3 Soldiers and Recovery Mission
3 soldiers who died in the terrorist attack that was likely a hijack.
We as criminals (from their perspective) have planned for a catastrophic event that intends to not leave a single individual alive, subsequently and naturally resulting in a "Recovery Mission".
How could we lay more elements of the puzzle that when the agency (CIA) looks back at them as they occurred in the past would make sense of them? Here’s what we can do:
What's the routinely route of that individual? We (as criminals) have intel that he goes to the library on Mondays (as an example).
Add a targeted sign that includes a certain element that represent a specific reference in the case hidden within the context of let's say a meeting in a conference room. But in this case, let’s do a strike match of those two elements in one targeted instance of implication.
Add a text on that sign as "Recovery College Courses” on “Floor 3" in that library where in a later date after the crash, the "Recovery" keyword will be attributed to the "Recovery Mission” and "Floor 3" would refer to the "3 Soldiers" that they planned beforehand to sacrifice in the crash.
This is similar to leading signs that aims to guide you from a place to another.
It becomes a "roadmap" based on the interactions of that individual who's connected in a way or another to the CIA to relay those pieces to the agency through.
As a person with acknowledgement of the case circumstances and the type of targeting you become naturally more skeptical about some of the signs and others from surroundings that you start questioning whether it is a normal sign from a perspective or was it purposely added to interpret another angle subject to the scope of the case and the timing in which other elements might have concurrently occurred at? Also, factoring the duality of things.
Puzzle piece 11
Runway 33
Based on the Jesus reference made in this article.
We as criminals are very powerful and Nazi that we make a "Jesus" example out of our victims.. No, in fact the entire American population in the event that another authority favors the citizens over our dirty manipulative business that we're just going to make a "Jesus" in a "33" in his age out of them (in a sense).
Now, throw the "33" number in every instance across all of our manipulative channels from manipulating the number of the impression count of a post the victim made on their social media profile to the percent of their phone battery every time they pick it up to be "33" and everything in between – but why not also perfectly align the American Airlines plane that we planned to crash to land on Runway number 33.
And because the 33 and Jesus are a spiritual topic, why not calling whoever alleges and attributes that to us to be a "spiritually possessed" or "haunted"?
But in reality they're leveraging the technological sophistication and their powers to apply such "Nazi" practices. That is how atrocious these crimes are. The “33” refers to the age of “Jesus” and the whole element resembles a sacrifice.
Puzzle piece 12
We Need More Reinforcers Pieces on The Puzzle..
From the criminal perspective..
Have the CIA Asset’s laptop's screen flashes “black” several times a few days prior to the attack in reference to the "Black" in "Black Hawk". Cybercrime.
Have the asset’s phone's screen also flash black 1 day prior to the attack to match with the laptop screen black flashes.
Two different devices, completely different operating systems yet the same exact phenomena occurred through cybercrime and surprisingly only few days prior to the attack.
Both of above points represent Puzzle piece 13
Post by Adel Andraws (former Boeing official) prior to the incident by 4 days. Click here to read the explanation surrounding the post. Puzzle piece 14
In fact, the overall analysis of those elements collectively, and particularly when factoring in the above sequential order and the suspected "electronic hijacking" of the Black Hawk, these created a link to another implicatory piece of text that was made in an earlier date by the high-rank former Boeing employee (Adel Andraws) that mentioned the terms "CONTROLLED" where he put it in uppercase form aside from the rest of his text, which could be the equivalent to a "controlled electronic hijacking" and was made for a future reference along with other terms, that is despite any other interpretations that may have been concluded about such term at that time, which could have also intended for a future reference.
Could a “Drone Jammer” video that was displayed to the CIA individual on one of the social media platforms just a few days before the incident was targeted and intended to deliver an implication of the suspected electronic hijack along with the above “CONTROLLED” in uppercase by the Boeing official?
We have seen those types of precise targeting throughout the whole case that these became the norm for a person to be able to interpret whether a video is targeted and could be correlated to the case or not.
Helicopters Campaigns
We are very powerful that we can even send targeted flying helicopters just like we do with cars, which are demonstrated in other articles and that is in correlation with the targeted pickup truck carrying the "Search and Rescue Helicopter" (puzzle piece 6).
The CIA individual narrates that ever since that particular instance occurred that "Helicopter Campaigns" started to fly over his apartment complex (yes, you read that right) and where he's located at everyday for several months with the purpose of relaying these to the CIA. He adds that the targeting is so precise and often that by the time he exited Costco on one day a helicopter was perfectly aligned over his head at a distance upon his exit.
What is the likelihood that all that number of helicopters fly over the individual at different locations, different times, precisely over the location where that individual of interest to the CIA is at unless these are targeting with an intent of certain "interpretation"?
What adds-up as an evidence on this is the timestamps of the documentations by the CIA asset individual in reference to those Helicopter Campaigns but also linking them to Adel Andraws (mentioned above). By linking this fact herein to the timestamped succession of elements by Adel Andraws in his post just a few days prior to the crash incident, and the whole sequential trail in whole, you will be able to form a holistic picture attributing the event to Adel and subsequently the criminal parties reported in the case. My apologies, I’m being impaired neurally and if it wasn’t for the neural impairment, I would have provided much clearer explanations and demonstrations of evidence.
Puzzle piece 15
Military Type Aircraft
As the case emphasizes on the possibility of engaging the "Military" within the country to abolish the ongoing "Riot" and enforce "Civil Order", the incident of crashing a “Military Type” of aircraft with a “Civilian” one comes as a retaliatory terrorist action following a consistent pattern by those criminal actors over the years.
The above is based on the invasive surveillance conducted by those criminal actors, which covers the CIA asset individual, allowing them to see and visualize elements from their surroundings. The individual coincidentally encountered "Military Personnel" several times on multiple occasions and, at other times, "Military Vehicles" throughout the timeframe in which the events of the case evolved, that is along with those speculations about “Military Intervention” to reestablish "Civil Order" in the country as seen on articles published by several news agencies particularly citing Trump’s revelations of leveraging the Military to fight the enemy from within.
As a result, it seems that such Military instances have been interpreted as a message by the criminal actors in which they acted upon with a retaliatory attack involving a Military Aircraft.
Puzzle piece 16
The Aftermath
We (from their criminal perspective) need reinforcers that come following the attack. We have connections in multiple news agencies, we also have control over social media accounts with a large audience base, either through direct access, through the platforms’ backend that we can alter modifications to posts or even cybercrime on the devices of the individuals with access to those accounts.
We'll cast "particular keywords" with significance within the scope of the case and/or from the pieces of the puzzle we previously formed, and relay them to CIA through their asset(s) to confirm attribution of the attack. Below are some examples.
News/Media Instagram Account(s):
To post “Helicopter started tracking at CIA” - regardless of the legitimacy of such but as long as CIA is referenced that would count as another piece towards the overall puzzle.
Instagram algorithm to prioritize the post to the CIA individual’s organic feed.
Puzzle piece 17
In a Relatable Collision
A few days after the Black Hawk attack incident, the Daily Mail made a post on Instagram about another collision event between Japan Airlines and Delta in Seattle, WA (the CIA asset’s hometown) describing it by a plane that has “sliced” into another, as shown below.
You would expect “wording” as an Airline that has “collided” with another, but not “sliced”, correct?
Surprisingly, such wording by the Daily Mail including “sliced” has came shortly after the CIA-linked individual has “privately drafted” a piece of text related to the case that included “slices” as a keyword. Again, the draft was not shared with anyone and within the scope of the case and the reported terrorist attacks. Screenshot below followed by the timestamp of the draft.
It was no coincidence that such post also topped the “supposedly” organic feed of the individual on Instagram.
Slice here, slice there, that leads us to the FBI post that featured another "slice" in the Bureau's "Pizza Connection" case (screenshot below) which was made 10 days after the above.
You Judge
What is the likelihood that all these distinctive elements co-exist in one single incident where each element was referenced in this corruption scandal case unless these were perfectly aligned and puzzled to fit perfectly towards such incident (terrorist attack)?
Alternatively, do these interactions and the successions of elements, forming obvious “consistent patterns” not raise a concern?
Read through the articles for more of these sequential patterns and other types of evidence. The blind would see them but the FBI (when/if reported) would not. Material that have been referenced in the article and were not added, will be included in a later date. Subscribe for updates.
List of Terrorist Attacks
Motivated by those criminal leaders.
Robb Elementary School Shooting
Club Q Shooting
The Covenant School Shooting
Apalachee School Shooting
LA Wildfires
Abundance School Shooting in Madison, WI
Black Hawk American Airlines Crash
Are Presidential Powers Required?
These criminal leaders backed by the FBI are ruling over the country, just behind the scenes, with so much corruption, injustices, and crimes against humanity from trafficking to modern slavery and torture, bribery schemes and many others.
They are silencing the right to justice and any attempt towards that by motivating for tragical events indirectly including mass school shootings, wildfires (arson) such as the recent LA wildfires as an example and many others across the United States, essentially jeopardizing the national security of the country.
Given such large threat landscape, presidential powers appear to be necessary; not to be confused with violence; however, Trump's indications about "invoking" of measures or "acts" that would permit the domestic deployment of the "Military" or "National Guard" to restore and maintain civil order within the country seems to be plausible.
See Also
Disclaimers
The information added herein and in other articles are true to the best of my knowledge, are my own opinions, based on my own observations, and do not necessarily reflect any of the ClA's or the Government unless explicitly stated by the agency, including but not limited to references made such as “CIA Individual” or “CIA Asset” and others.
The law governs these types of engagements, which allow the CIA to either confirm, deny, or state that it can do "neither" confirm "nor" deny involvement.
No authority shall take an action against me for publicizing these matters based on the disclaimers herein, as they may be true, and are protected by Free Speech laws.
I exercise my right to free speech, and my statements are protected under freedom of speech and expression laws.
All disclaimers added to the referenced articles and documents shall apply with perseverance to supersedence in the event of conflict, at my sole discretion.